Information security is playing a significant role in everyone’s life. Data is collected, used, and demolished every second. Data is the biggest asset in our world such that it has replaced oil. Where data (PII) is collected, there are always risks and organizations are expected to protect it. If they fail, they do not just lose the data, but also their reputation, market shares, leadership, and value.
Breach Summary:
A popular example of data compromise would be the Equifax breach, which was announced on September 7th, 2017. It impacted 145+ million U.S. consumers. The attack started in May 2017 and was identified by Equifax in July 2017. The information, which was embezzled from Equifax’s database included: Customer’s names, Social Insurance Numbers, Date of birth and in some cases Driver’s License numbers. As per Equifax, there was a flaw in the Apache Structs 2 software (CVE-2017-5638). A vulnerability was discovered in March by Apache Structs, and a patch was released on March 8, 2017. However, Equifax failed to update/patch Apache Structs 2. Subsequently in May 2017, attackers breached Equifax’s database and remained unidentified for 76 days in their network. Equifax discovered the breach in July 2017 and then officially announced it in September 2017. Equifax shares dropped by 13% and the following points lists some headline news.
Major reputation hits on Equifax in tech community and news.
· “Why the Equifax breach should never have happened”. (https://techbeacon.com/security/why-equifax-breach-should-never-have-happened)
· CEO Richard Smith who oversaw breach to collect $90 Million (https://news.slashdot.org/story/17/09/29/143209/equifax-ceo-richard-smith-who-oversaw-breach-to-collect-90-million)
· “Equifax CIO, CSO “retire” in wake of huge security breach”. (https://arstechnica.com/tech-policy/2017/09/equifax-cio-cso-retire-in-wake-of-huge-security-breach/)
· “Breach was entirely preventable”, “Lack of accountability and management structure”(https://republicans-oversight.house.gov/report/committee-releases-report-revealing-new-information-on-equifax-data-breach/)
The timeline of the breach illustrated:
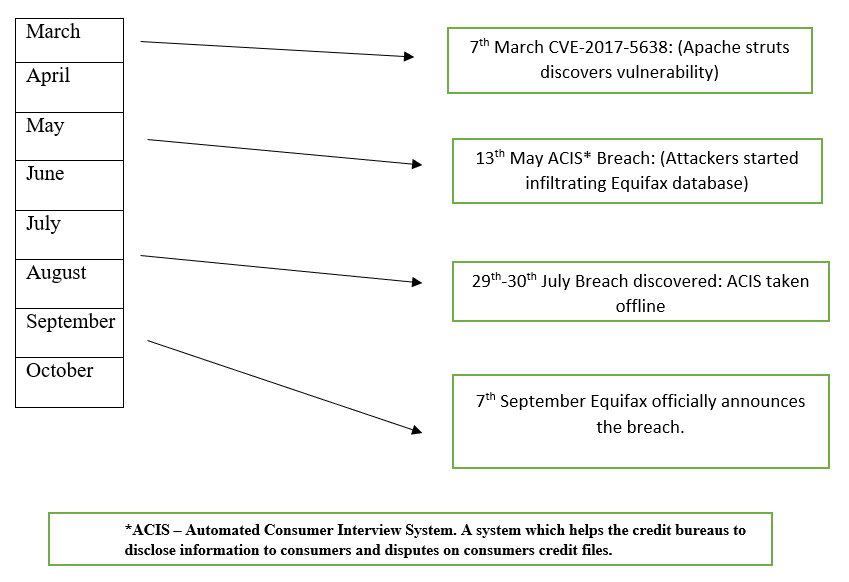
In this situation, the attackers were able to exploit ACIS, which uses Apache Struts 2. Due to the vulnerability (CVE-2017-5638), they were able to drop some web shells via an exploitation, and in so doing, were able to infiltrate Equifax’s system. The attackers proceeded to conduct more than 9000 queries against 51 databases and was able to read a .txt file, which had usernames/password of other systems. The attackers remained unidentified, and had access for more than 76 days, which resulted in stolen data. Equifax failed to detect the breach, because the SSL certificate on a device which allows them to see encrypted traffic had expired since 2016, and which was not noticed by the in-charge personnel. After the update of new SSL certificates, they were able to track the traffic. In my opinion they could have changed the setting from the beginning, where they can see the traffic flow even if the certificate expires. After the updates, Equifax noticed suspicious traffic from an IP address in China. After testing, they decided to take the ACIS system offline.
Now the question is, what is the big deal on the vulnerability? Apache Struts 2.3.5 (which was released in 2012) to 2.3.31 were vulnerable since 2012, and the 2.5 series till 2.5.10.1 had the same vulnerability. In this vulnerability, if there is error in content-type in the http header, and when it attempts to handle the error, it generates an error message which allows it to run the arbitrary code. (#cmd=string)
In simple words, it is easy to find vulnerable systems with different scanners, anyone could copy and paste the commands with scripts and run it to exploit. It becomes the most important task to keep the systems updated/patched. Even with the advance systems e.g., Firewalls, IDPS, logging and monitoring with many security professionals handling the system, Equifax was still breached. In my opinion, even if the vulnerability was not updated, they could have prevented the breach by restricting traffic from suspicious IP addresses.